This guide provides a list of the top 10 phishing websites online, as well as information and tips on how to identify and avoid phishing attacks, and how to protect personal information and business data from cyber threats. In this guide, IT Exams emphasizes the importance of staying vigilant and cautious of suspicious links and emails and offers practical advice on how to stay safe online. Whether you’re an individual or a business owner, this guide provides valuable insights and best practices to help you stay protected from the risks of phishing attacks.
What Is Phishing? How Does Phishing Work?

Phishing attacks rely on several types of information, ranging from personal to political. Tattackers regard the present COVID-19 outbreak as an opportunity to profit financially. Because the public relies heavily on digital media for information and guidance concerning the epidemic, they are vulnerable to phishing attacks conducted by threat actors. Using the most recent news bytes, for example, could trick users into clicking on malicious links and downloading attachments that install malware on their devices. The number of steps in these processes varies depending on the type of phishing attack. The most modern approaches entail the use of artificial intelligence (AI), which can record and analyze the voice pattern of an organization’s head and reconstruct a call with endless responses to authorize and command an immediate transfer of a large sum of money.
What Is The Aim Of The Phishers?

Any hacker’s motivation for attempting a cybercrime can range from financial motivation to state-sponsored motivation, with the former accounting for 71% of all incidents. Public, information, and financial services are the three industries most affected by phishing. As previously said, phishing assaults are only the initial stage of a sophisticatedly constructed broader attack, and subsequent attacks such as malware deployment, ransomware, and so on are significant elements of the cyberattack. However, the capacity of these follow-up attacks to cope with system damage is dependent on the success of a phishing attempt. As a result, it is not uncommon for Google to block over 100 million phishing emails per day as hackers attempt to steal important information and introduce destructive malware.
Types of Phishing Attacks
Any phishing assault can be divided into one of the following groups based on the various modes it employs and the various procedures involved:
1. Spear Phishing
This sort of phishing uses customized emails/campaigns that are tailored to a specific target’s interests in order to appear more relatable and less suspicious. To accomplish this, the attacker must conduct extensive reconnaissance in order to collect as much information about the victim as possible. The useful information gleaned from the reconnaissance can include things like names and emails of persons the target knows, giving the target the false impression that they know who sent the email.
2. Smishing
SMS phishing (thus the name Smishing) is used in this sort of phishing. Mobile-based phishing attacks are more widespread. It is one of the oldest and most well-known hoaxes, in which the threat actor uses lottery schemes to entice less educated victims.
3. Whaling
Whaling is a sort of spear phishing assault that targets a likely victim with the potential for higher financial advantages. Senior executives and other high-profile individuals with greater trust, access, and influence within a business, such as C-Suite executives, are examples. The usage of AI outlined above might also be classed in this category.
4. Clone phishing
Clone phishing is an email-based phishing attempt that includes significant reconnaissance, with the phishing email being generated based on its output. If a previously transmitted genuine email between two parties is leaked, its contents could be used to construct a similar or cloned email. The prior email’s attachment or link is then substituted with malicious URLs or attachments and delivered to the recipient from an email ID with a similar domain address as the original counterpart. This email would typically come as a resend or follow-up to the original.
5. Uplink manipulation
Most traditional phishing emails include link manipulation, in which the original link in the email is replaced with a malicious one. This might possibly be expanded into website forgery. Misspelling URLs or employing subdomains is a typical phishing technique, and the majority of the link remains intact. The attack exploits the normal human practice of not reading the entire link and its decryption.
6. Filter evasion
Phishing emails must avoid being detected by mail filters (also known as spam filters) and routed to the trash/spam folder. Some of the less complex evasion strategies involve the use of images interspersed with malicious links rather than text, making them more difficult to detect, because simple spam filters rely on different (spam) words in their repository to recognize and categorize whether a letter is real or spam.
7. Website forgery
As the name implies, scammers develop phony websites that look identical to the real, or they use JavaScript commands to change the address bar of the malicious website to make it appear legitimate. Existing weaknesses in an original website’s scripts can sometimes be used by attackers to hijack the webpage itself. This form of attack, also known as cross-site scripting, encourages the user to sign in (which is typical of the original site’s behavior). Everything appears to be correct, from the web domain to the security certifications, but the website has been injected with malicious JavaScript, making it impossible to recognize without professional understanding.
8. Covert redirect
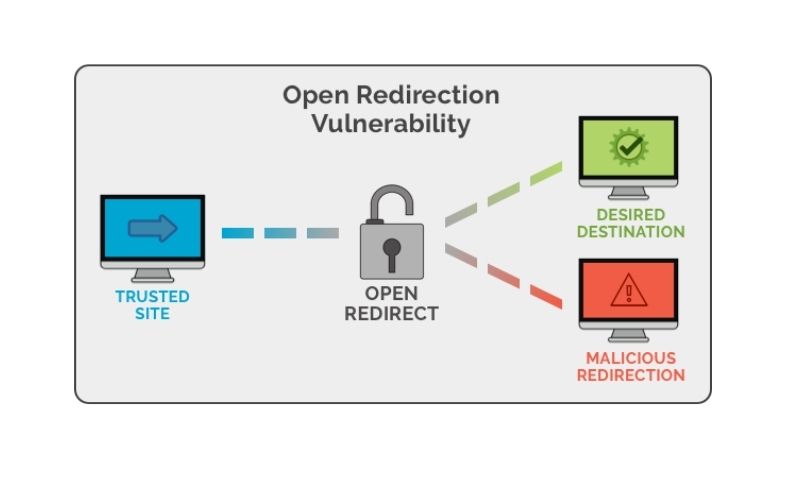
Covert redirect is a more complex and advanced kind of website forging in which the user is initially sent to a valid website but is subsequently redirected to a hostile website. Malicious browser extensions/cookies are sometimes used to discreetly redirect users to phishing websites. This is only possible if the attacker already has control of the website.
9. Social engineering
Though social engineering is a broad issue, the extent to which it is used in phishing attempts has led to its classification as one of its numerous categories. Social engineering employs psychological manipulation to dupe people into disclosing sensitive information by clicking on a malicious link or downloading an attachment. For example, the recent COVID-19 pandemic has piqued the attention of many people in reading healthcare-related news and updates. As a result, several threat actors have created false news, blogs, health updates, or maps in order to entice consumers to click on such links.
10. Voice phishing
Not all phishing attempts necessitate the use of a bogus website or email. Voice phishing or Vishing refers to calls that purport to be from a bank or a reputable institution and push users to divulge sensitive and financially damaging information such as account numbers, PINs, passwords, and so on. As previously stated, the usage of AI has resulted in some astounding achievements in this field.

Of all the phishing attacks mentioned above, there a is need to discuss phishing emails especially.
Because Emails often contain confidential information. Some emails may contain sensitive information such as personal data, financial information, trade secrets, or confidential business information that needs to be protected from unauthorized access or disclosure. Phishing emails are sent by scammers to trick people into sharing their sensitive information such as passwords, credit card numbers, and other personal data. The main goal of these scammers is to gain access to your accounts or steal your identity for financial gain or other malicious purposes.
Phishing scams are becoming more sophisticated as well as more common. We’ve provided examples of some of the most common and successful phishing emails available. Take a look, share, and stay away.
1. The fake invoice scam
Let’s begin with what is likely the most popular phishing template available: the fake invoice technique. This scam, like many others, is based on fear and urgency, forcing end users to pay for items or services they have never ordered or received.
Finance departments are the obvious targets for this type of attack, but there are many possible victims who could be taken in.
2. Email account upgrade scam
When your account is about to expire unless you take fast action, the email account upgrade scam may look to be from a reliable email provider like Microsoft or Google, or even from your company’s IT department. Phishing for email account upgrades
As you can see, there is nothing hazardous in this email. There are no obvious grammatical problems or demands, and the link itself appears to direct an unsuspecting visitor to a secure “https” web page. When requested for personal information, it’s a good idea to linger over the link itself, as the language often doesn’t represent the exact destination of the link.
3. Advance-fee scam

Perhaps receiving an email from a foreigner pleading for your assistance in recovering a lost sum of money is a ridiculous reason for an elaborate story. But don’t be deceived; this fraud has been around for a long time for a reason: it works.
The fraudster will offer you a significant number of money in exchange for your bank account information in the email. Not only will you not receive a dollar from this generous Prince, but a portion of your money will be directed in the opposite way.
4. Google Docs scam
The Google Docs scam, one of the most recent high-profile phishing schemes, has an extra deadly twist in that the sender can often look to be someone you know. Phishing scheme using Google Docs
This smart email invites you to click on a link to view a ‘paper,’ which then redirects you to a virtually identical version of Gmail’s login page. Once you’ve chosen an account, you’ll be asked to allow access to your Google account, which means the attacker has complete control.
5. PayPal Scam
With over 200 million users, PayPal is a highly profitable tool for cybercriminals. In addition to its large number of accounts, PayPal allows fraudsters to use a platform that is directly linked to their credit card or bank account.
These emails frequently include the PayPal logo, as well as a convincing section of small language at the bottom. Again, this scam attempts to induce panic in its victims, frequently with a “There’s a problem with your account, please click here to fix it” message. Beware, they also have what appears to be legal fine print.
6. Message from HR scam
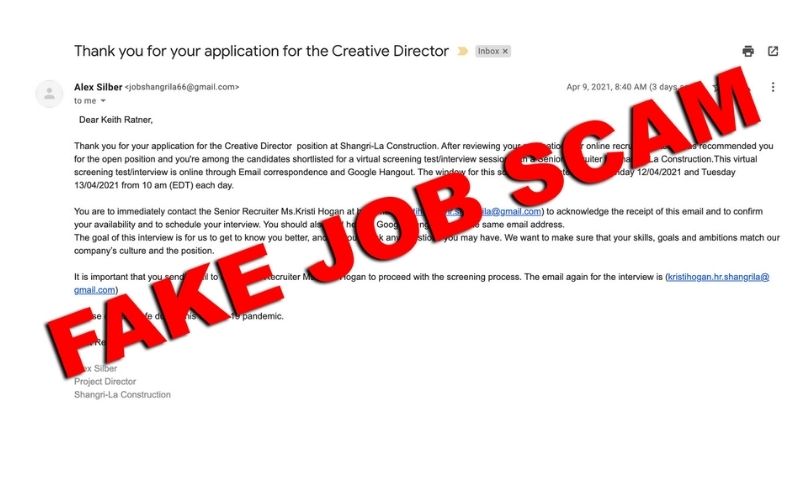
We all (ideally) trust our HR department, especially when it comes to receiving critical emails on company-wide or personal changes. The issue is that cybercriminals are well aware of how much trust we invest in our HR professionals.
An HR email scam frequently includes a malicious file or link that, when opened, installs dangerous software into your computer or device. Encourage colleagues to immediately question the HR sender whether a request for personal information is legitimate before pushing the send button.
7. Dropbox scam
The same old scenario of enticing users to click a link, but with a completely new platform to employ. Dropbox, the online sharing and storage tool, has increased in popularity in recent years, and so have its imposters.
The Dropbox phishing email often operates by informing the user that the ‘file’ that has been emailed to them is too large and must be opened with a quick “click on this link”. You’ve undoubtedly figured by now that a bogus Dropbox landing page is on the way… and you’d be correct. What you might not have guessed is that this page can be found within Dropbox itself, patiently awaiting your information.
8. The council tax scam
The council tax scam is a particularly aggravating attack because it can employ a variety of creative messages to get you to give over your information.
Here are a few more samples of what a bogus tax email may contain, taken from the UK Gov website:
- It claims you are in the incorrect Council Tax band and owe past payments on your Council Tax bill, even though your band is accurate;
- It claims to be from the local council or the Valuation Office Agency (VOA) and requests your bank information in order to issue a refund;
- Make a claim that the VOA costs you to contest your Council Tax band;
- Claims that taxpayers must be represented by an agent by law in order to contest their band.
End customers are encouraged to follow the link contained inside the email to be sent to a reputable page (e.g., Microsoft) where they can easily update their password. However, any credentials submitted to this page will be forwarded directly to the cybercriminals in question.
9. Unusual activity scam
When you receive an email or text announcing that there has been “suspicious activity on your account,” the alarm bells go off. That’s why this fraud works so well for scammers: victims are confronted with not only hurry and terror but also bewilderment.
This is only one example of a possible odd activity fraud. An attacker can employ this destructive tactic on any app, website, or platform, including your bank or Instagram account.
What Is A Phishing Website?
A phishing website is one that fraudsters utilize for nefarious goals such as credential theft or financial fraud. People commonly visit phishing websites after clicking on a malicious email’s phishing link. Phishing websites can be developed with faked or lookalike domains or as part of a compromised legitimate website (a social engineering method known as water-holing).
Cybercriminals can utilize phishing websites in a variety of ways. For example, the target may be presented with a log-in screen to enter their credentials, which are then scraped by the cybercriminal for use in account takeover attacks; or they may be prompted to enter payment details to confirm an order or pay for an item that will never arrive, or they may even download malicious files automatically or via a prompt on the webpage.
Top 10 Phishing Websites Online
There are many free phishing sites on the Internet that can be found easily. Below are the top 10 phishing websites online that you can refer to. Let’s take a look!
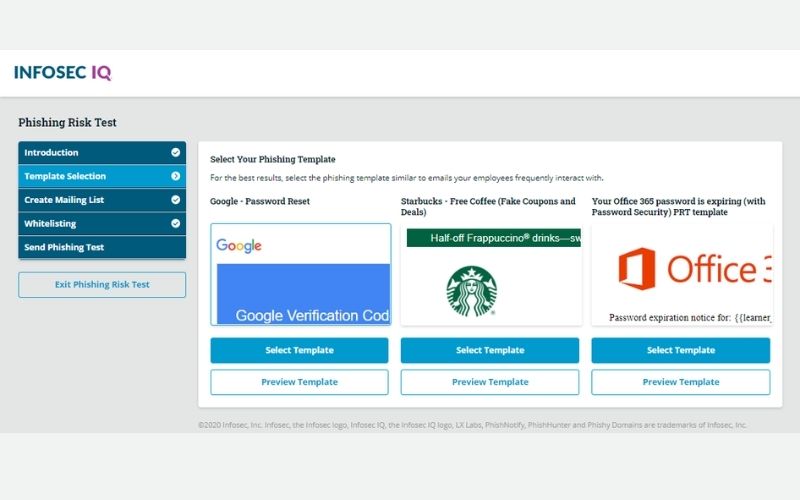
1. Infosec IQ
Infosec IQ by Infosec is among the top phishing websites. It provides a free Phishing Risk Test, which allows you to quickly conduct a simulated phishing campaign and receive your organization’s phishing rate within 24 hours.
PhishSim, Infosec IQ’s full-scale phishing simulation tool, can also be used to run sophisticated simulations for your entire enterprise. PhishSim has over 1,000 phishing templates, attachments, and data entry landing pages in its repository. PhishSim templates are updated on a weekly basis, allowing you to train your personnel on the most recent phishing attacks. Do you want to create your own phishing emails? PhishSim has a drag-and-drop template builder that allows you to create phishing campaigns to
2. Gophish
The runner-up on the list of top 10 phishing websites is Gophish. Gophish gets it right as an open-source phishing platform. Most OS systems support it, installation is as simple as downloading and extracting a ZIP archive, the interface is straightforward and intuitive, and the capabilities, while restricted, are well-thought-out. Users can be added manually or in bulk via CSV import. Email templates are simple to create (there aren’t any included, but a community-supported repository is set up), and modify (using variables allows for easy personalization), campaigns are simple to set up, and reports are appealing to the eye and can be exported to CSV format with varying levels of detail. There are no awareness education components, and there are no campaign scheduling possibilities.
3. LUCY
The first commercial product on our list, LUCY, makes it simple to get the platform’s free (community) edition. You only need your email address and name to download LUCY as a virtual appliance or a Debian installation script. The web interface is appealing (if a little complicated), and there are numerous features to investigate: LUCY is intended to be a social engineering platform that is more than just phishing. There is also an awareness component with interactive lessons and quizzes. So, why didn’t we put LUCY at the top of the list? Because we’re talking about free phishing simulators, and the community version of LUCY has too many constraints to be useful in a business setting. Some critical capabilities, such as exporting campaign stats, launching file (attachment) attacks, and, most crucially, campaign scheduling options, are not available under the community license. As a result, the free edition of LUCY provides you with a taste of what the expensive version can achieve, but it doesn’t go much further.
4. Simple Phishing Toolkit (sptoolkit)
While this solution may not be as visually appealing as some of the previous entries, there is one key element that propels it to the top of our list. With a feature that (optionally) redirects phished users to a landing page with an awareness education video, Simple Phishing Toolkit allows you to combine phishing tests with security awareness education. There is also a tracking option for users who have finished the program. Unfortunately, the sptoolkit project was shelved in 2013. A new team is attempting to resurrect it, but documentation is scant and distributed over the internet, making realistic implementation in an enterprise environment challenging.
5. Phishing Frenzy
While this open-source Ruby on Rails application is intended to be a penetration testing tool, it includes a number of characteristics that might make it a useful tool for internal phishing campaigns. The ability to view extensive campaign stats and simply save the information to a PDF or an XML file is maybe the most crucial feature. You may probably predict what the “however” section is going to be: Phishing Frenzy is a Linux-based application that requires expert installation.
6. King Phisher
Ranked 6th in the list of top 10 phishing websites online in this guide is King Phisher. The features of King Phisher are numerous, including the ability to execute multiple campaigns at the same time, geolocation of phished users, site cloning capabilities, and so on. Templates for both messages and server pages are stored in a separate repository. The user interface is sleek and straightforward. However, installation and configuration are not so simple. The King Fisher server is only supported on Linux, and depending on the flavor and existing configuration, additional installation and configuration steps are required.
7. SpeedPhish Framework (SPF)
Adam Compton produced another Python utility. SPF provides a number of tools that allow you to swiftly create and execute effective phishing attacks, such as a data entry attack vector (3 website templates are supplied, with the option of utilizing custom templates). While a tech-savvy security professional can have a lot of fun with SPF and run phishing campaigns against multiple targets, it is still primarily a pen-testing tool, with many great features (such as email address gathering) being unimportant for someone performing internal phishing tests.
8. Social-Engineer Toolkit (SET)
Another tool from TrustedSec, this one was meant to undertake various social engineering assaults, as the name implies. For phishing, SET allows you to send spear-phishing emails as well as mass mailer campaigns, as well as some more complex capabilities like labeling your message as important and uploading a list of target emails from a file. SET is written in Python and has no graphical user interface. It is an excellent penetration testing tool. It is fairly limited as a phishing simulation system, with no reporting or campaign management features.
9. SpearPhisher BETA
This tool among the best phishing sites is not attempting to deceive anyone (except its phishing targets). SpearPhisher, created by TrustedSec, says it all in the description: “A Simple Phishing Email Generation Tool.” With a focus on simple.’ SpearPhisher is a Windows-based software with a simple user interface that is intended for non-technical users. It lets you easily create a phishing email with personalized From Email, From Name, and Subject fields, as well as a WYSIWYG HTML editor and the opportunity to send one attachment. You can send the created email to many recipients by entering their email addresses in the To, CC, and BCC areas. The program has been in Beta since 2013, thus no upgrades are likely in the near future.
10 . Lodestone Offensive Services
Lodestone Offensive Services helps organizations to leverage threat actor tactics, techniques, and procedures (TTPs) by testing their environments against real-world attacks without risking their critical data and business flow. Their penetration tests go beyond standard vulnerability assessments by performing proof-of-concept exploitation of vulnerabilities safely through the team of white hats. Lodestone’s experts set up the organization for success by hardening their environment with TTPs observed in the wild, identifying potential security weaknesses, and providing recommendations for remediation. The company’s security posture is strengthened from Active Directory to physical security, insider threats, and beyond, including key components of their business such as web applications. They also work with the organization to put their mind at ease by testing against headline-making cyberattacks like ransomware and phishing.
6 Tips For Identifying Fraudulent Websites
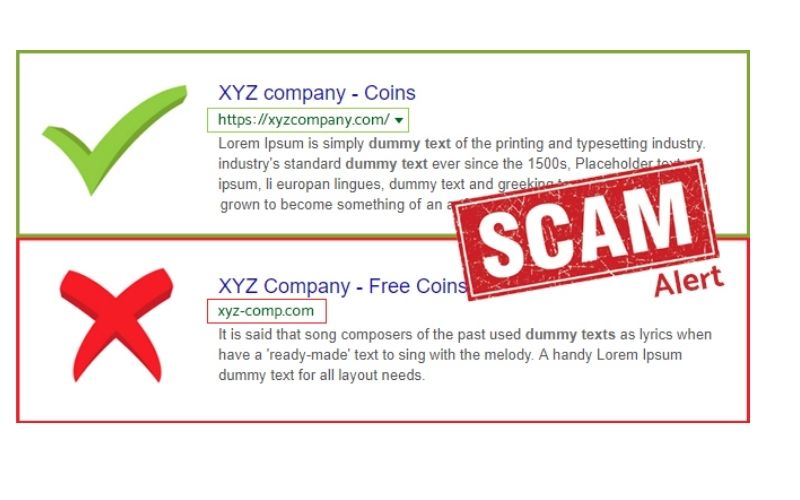
Check the URL
xamining the URL is one of the first measures you should take to determine whether a website is legitimate. The address bar should include a padlock icon, and the URL should begin with ‘https://’ or’shttp://’. This means that the website has been encrypted and secured using an SSL (Secure Sockets Layer) certificate.
Another thing to consider is the spelling of the web URL. Cybercriminals take advantage of people’s proclivity to skim-read information. As a result, to begin their phishing attempts, they would construct web addresses that are similar to well-known and trusted ones. For example, a web address that generally ends in ‘.org’ could be altered to ‘.com’, or letters could be replaced with numbers.
Redirects to phishing websites, including URL shorteners
Be careful that if you clicked on a seemingly legitimate link in an email or SMS message, you may have been sent to a bogus site. To mask their malicious URL, the cybercriminal can use content that appears benign (the URL for a legitimate website or even a prompt like ‘Sign in’).
Cybercriminals executing complex assaults can also use redirects once an email has been delivered to try to avoid detection. This is referred to as post-delivery weaponization.
Similarly, URL shorteners can be used to conceal the phishing link, and legitimate services can be exploited to evade detection. The text within the phishing email will contain the shortener URL, which when clicked will redirect to the fake website.
Even if you’ve clicked on a seemingly harmless URL, you should be wary of phishing.
Take a close look at the content

Is the website’s appearance subpar, such as low-quality photos or branding (including logos), or bad spelling and grammar? This could indicate that you’re on a phishing website.
Most reputable firms will spend a significant amount of money and time on a well-designed and highly polished website with the correct language, sharp images, and a logical user experience.
Here are a few frequent red flags to check for:
- Simple spelling and grammatical errors
- Language that is subpar (for example, broken English)
- Images with low resolution
The absence of a ‘contact us’ page is another sign that you are on a phishing website. Genuine businesses frequently include contact information such as their physical address, phone number, email address, and social media links. If this is missing, proceed with caution. While the absence of contact information can still be used to identify a phishing website, some fraudsters develop basic ‘contact us’ pages or add this information to the webpage footer to make their attacks appear more authentic. The authentic brand’s information may be taken from elsewhere and used on the phishing website in templated brand imitation attacks.
Think about your journey
Did you go directly to the website, use a search engine, or click on an email link? If you have any worries about the legitimacy of a website and reached there by clicking a link, re-enter it by typing known addresses (e.g. ‘www.amazon.com’) into your browser or searching the brand name via a search engine.
Even if you believe the email is from a credible source, if you weren’t expecting it, take the two preceding procedures to validate the website (and if in question, navigate to another way or contact the sender using a method other than the original email).
In this case, bookmarking your frequently visited websites once you’ve verified their validity is a fantastic way to avoid a successful phishing attack. That way, you’ll know you’re in the appropriate spot and won’t fall victim to phishing attacks impersonating those brands.
If it’s a new website that you haven’t visited before, take the time to manually visit it using your usual browser and make sure there’s nothing hazardous about it using suggestions like those in this article.
Read reviews

It’s always a good idea to do your homework on a company to see whether they’re who they say they are and to verify their reputation. If the website has previously scammed visitors, the victims’ experiences may have been posted online.
Because favorable comments can be easily fabricated, it’s best to check reviews from multiple reliable sources. Here are some methods for detecting bogus feedback:
- There are many curiously similar reviews: perhaps they all have a similar writing style, describe everything in the same manner, or have given the same review and rating on several sites.
- The following profiles were recently created by the reviewers: Look for evaluations from more established members of the review website; if they’ve reviewed hundreds of websites, they’re more likely to be a reliable source of information.
- There haven’t been many reviews: This could simply be due to the company’s inexperience; nonetheless, if you’re already skeptical and there isn’t much online criticism, skip the website.
Check payment methods
A trustworthy website will accept credit/debit cards or regular payment methods such as PayPal. However, it is usual for phishing websites to require a bank transfer or Bitcoin payment.
If you use a credit or debit card to make a purchase that turns out to be part of a scam, you have a better chance of getting your money back. However, if you paid by bank transfer, there is generally little you can do. Legitimate firms will never request bank transfers, so avoid sending money this way.
Find out who owns the website
Because every domain must be registered, it’s always a good idea to do a background check to determine who owns it. This information, as well as their contact information and the date their website was created, may be found here. You can also utilize search engines to see if there have been any reports of the website being used in cybercrime schemes (or even lower-level scams).
Phishing websites have gotten more convincing as fraudsters develop their attacks to escape detection and to make them more appealing to their target, with many utilizing sophisticated impersonation techniques.
Checking the origin of the domain, on the other hand, allows you to determine factors such as domain age (has it been around for a long time, like the legitimate brand, or is it a new site? ); what country the domain is registered in (checking whether that tallies with information you know about the legitimate company, such as where they operate or where their headquarters are located); and who it is registered to (checking whether that matches the information you know about the brand (foolproof).
If your investigation raises any red flags, it’s advisable to navigate to a reputable brand website in a different way or to skip the website entirely.
FAQs

Is it illegal to make a phishing site?
Yes, it is unlawful to create a phishing website. Several federal and state (U.S.) laws prohibit phishing. To begin with, most people associate phishing with not only the development of a website but also the act of sending an email.
What is the number 1 phishing attack?
The most common sort of phishing attempt is email phishing. In an email, cyber thieves impersonate businesses or organizations, prompting potential victims to click a link and provide personal information or pay for something. Cyber attackers can view any data input, including passwords.
Is phishing worse than spam?
When comparing phishing with spam, it’s vital to remember that phishing emails attempt to trick a user into exposing personal information, which is significantly more dangerous than spam because spam is typically commercial and not especially malevolent.
What is a phishing attack website?
A phishing attack website is a domain that looks and sounds similar to an official website. They are created in order to deceive someone into thinking it is legitimate. Phishing tactics have become increasingly varied and potentially hazardous in recent years.
Final Words
In conclusion, we have highlighted the top 10 phishing websites online that you can find easily. Besides this comprehensive guide provides quite a lot of information on types of phishing attacks, common email phishing, and how to mitigate those phishing attacks. By understanding the tactics used by phishing websites, we can take steps to protect ourselves from falling prey to these scams.
Remember to always verify the authenticity of a website before entering sensitive information, use strong passwords and two-factor authentication, and report any suspicious activity immediately. By staying vigilant and informed, we can protect ourselves and others from the dangers of phishing. Thank you for reading and stay safe online.