Wondering “What is a security operations center?” Looking to improve your organization’s security posture? Learn what a security operations center (SOC) is and how it can benefit your organization. In this comprehensive guide, IT Exams will discover everything from the primary functions of a SOC to how to build and maintain one. Discover how a SOC can help you mitigate security threats and keep your organization secures.
What Is A Security Operations Center?

A security operations center (SOC – pronounced “sock”) is simply a group of professionals that proactively monitor an organization’s capacity to function safely. A SOC has traditionally been regarded as a room where SOC analysts collaborate. While this is still true in many businesses, the introduction of COVID-19 and other causes has caused the SOC team to be more widely dispersed. Today’s SOC is becoming less of a solitary room full of personnel and more of a critical security role within a business.
A member of the SOC team may frequently perform just as effective working from home as they do in a physical security operations center.
What Does A SOC Do?

Members of a SOC team are responsible for a variety of activities, including proactive monitoring, incident response and recovery, remediation activities, compliance, and coordination and context.
Let’s take a deeper dive into each of these tasks.
Proactive Monitoring: This includes log file analysis. Logs can come from endpoints (e.g., a notebook computer, a mobile phone, or an IoT device) or from network resources, such as routers, firewalls, intrusion detection system (IDS) applications, and email appliances. Another term for proactive monitoring is threat monitoring. SOC team members work with various resources, which can include other IT workers (e.g., help desk technicians), as well as artificial intelligence (AI) tools and log files.
Incident Response and Recovery: A SOC organizes an organization’s capacity to limit harm and communicate effectively in order to keep the organization going after an incident. Viewing logs and issuing alarms isn’t enough. Helping companies recover from incidents is an important element of incident response. That recovery may entail tasks such as dealing with acute malware or ransomware situations, for example.
SOC team members do data-driven analysis to assist organizations in addressing vulnerabilities and adjusting security monitoring and alerting solutions. A SOC member, for example, might advocate a better network segmentation plan or a better system patching regimen based on information received from log files and other sources. A SOC’s primary mission is to improve existing cybersecurity.
Organizations safeguard themselves by adhering to a security policy as well as external security standards such as ISO 27001x, the NIST Cybersecurity Framework (CSF), and the General Data Protection Regulation (GDPR). (GDPR). Organizations require a SOC to assist guarantee compliance with critical security standards and best practices.
Above all, a SOC team member assists a business in coordinating various aspects and services and providing visualized valuable information. One aspect of this coordination is the capacity to create a helpful, usable collection of narratives for network activity. These tales aid in the development of a company’s cybersecurity policy and posture for the future.
A member of the SOC team assists a company in determining the root causes of cyberattacks. A SOC analyst is considered to be performing root-cause analysis when they do this. In a nutshell, a SOC analyst seeks to determine when, how, and even why an attack was effective.
To that goal, a SOC analyst examines attack evidence. This type of information is known as an indication of assault. If an attack is successful, a SOC analyst will investigate signs of compromise to assist the company in responding effectively and making changes to prevent such attacks in the future.
How Does A SOC Operate?
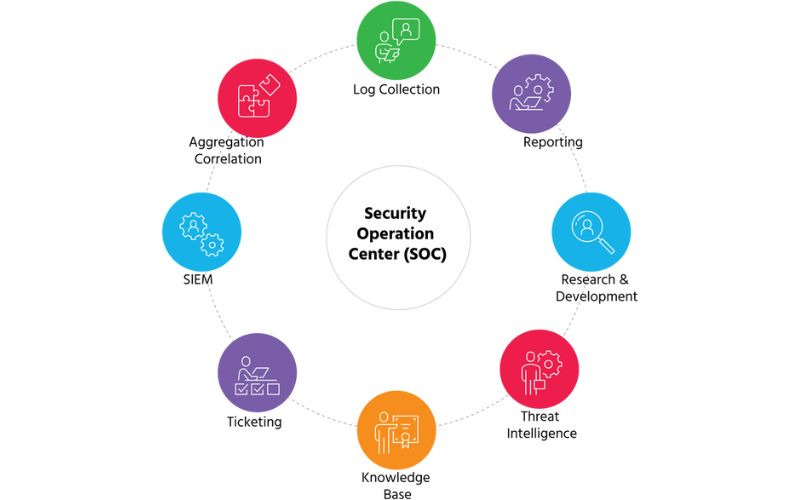
To begin, a SOC team receives information from multiple sources, such as CTI threat feeds and log files from systems throughout the company. A security operations center (SOC) staff closely monitors a company’s assets, which range from on-premise servers in data centers to cloud resources. Monitoring accuracy is crucial. As a result, members of the SOC team will monitor servers, endpoints, and perimeter devices such as firewalls and switches.
SOC team members then carefully analyze this data to provide actionable knowledge. Part of this interpretation is removing duplicate data and determining the core causes of problems. This is commonly referred to as data normalization.
Viewing the log files of a SIEM instrument is insufficient. The worker must have sufficient expertise and intelligence to appropriately evaluate data. In many respects, the ideal SOC team member serves as an information translator.
However, the SOC’s obligations do not end there. The SOC is not just tasked with tracking out the bad guys. Members of the SOC team spend a significant amount of time identifying factors that make perfect feeding grounds for hackers.
This includes looking for the following things:
- Unpatched servers and endpoints: While patching a system may appear to be a simple task, it is not. A member of the SOC team can assist in identifying unpatched systems or alternate courses of action. For example, if a system cannot be quickly patched for any reason, it may be required to monitor unpatched systems until time to properly patch it is available.
- Vulnerable endpoints: These are those that have outdated virus definitions or no antivirus at all.
- Perimeter and edge devices that exhibit neglect characteristics: These might include routers, switches, and other network equipment on or near your network that are not properly maintained and protected.
- End-user activity reports include: Hackers typically acquire unauthorized access to corporate information and resources through social engineering. As a result, SOC members work hard to keep individuals from being deceived by hackers.
As a part of the SOC team, it is extremely conceivable that you may
What Are The Types Of SOC Models?
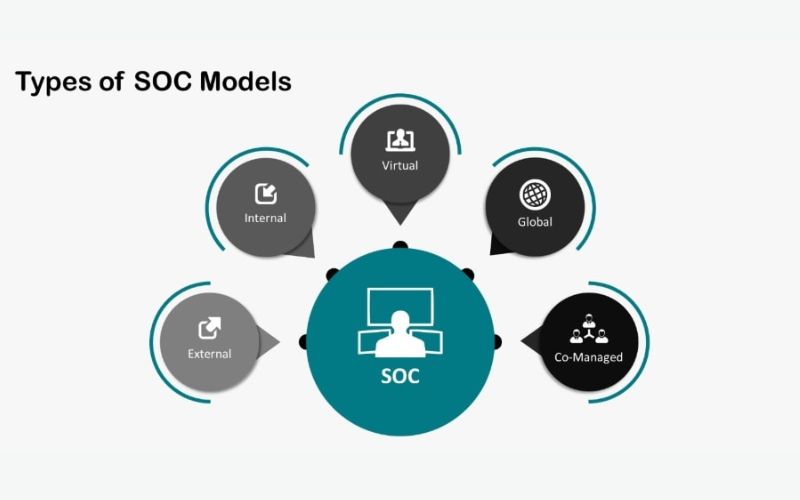
Fundamentally, companies can utilize one of three SOC models:
Fully insourced
In a fully insourced SOC, all security monitoring is handled by the organization’s workers. Its fundamental advantage is that the organization retains its entire operational accountability and control. Unfortunately, this is also its biggest weakness. The company must recruit and maintain people to operate the SOC, as well as the software and hardware utilized by the SOC, under the completely insourced SOC model. Typically, the acquisition of hardware and software licensing necessitates CAPEX in the first year and OPEX in the following years. This strategy is more expensive, but it provides the most configurable monitoring framework because everything is within the organization’s control.
Fully outsourced
Security monitoring is conducted solely by a third-party organization in a fully outsourced SOC. Its key advantage is that it is usually just plug-and-play. The organization selects a supplier and a monitoring plan that meets its requirements. This strategy normally does not require any CAPEX and is wholly supported by OPEX. Its main downside is that it forces companies to select from a list of alternatives provided by a service provider, which may or may not directly fit their goals and budget.
Hybrid
Security monitoring in a hybrid SOC is done by a collaboration between an in-house team and an external team. Its key advantage is that it allows you to handle all parts of the core monitoring function without having to pay for all hours of coverage in-house. Because contract staff for after-hours coverage is frequently less expensive than full-time, devoted employees, this strategy has lower OPEX than a fully insourced SOC. The biggest downside of this strategy is the additional management burden necessary to functionally integrate the two teams, guaranteeing constant coverage across the insourced and outsourced teams.
8 Benefits Of A Security Operation Center
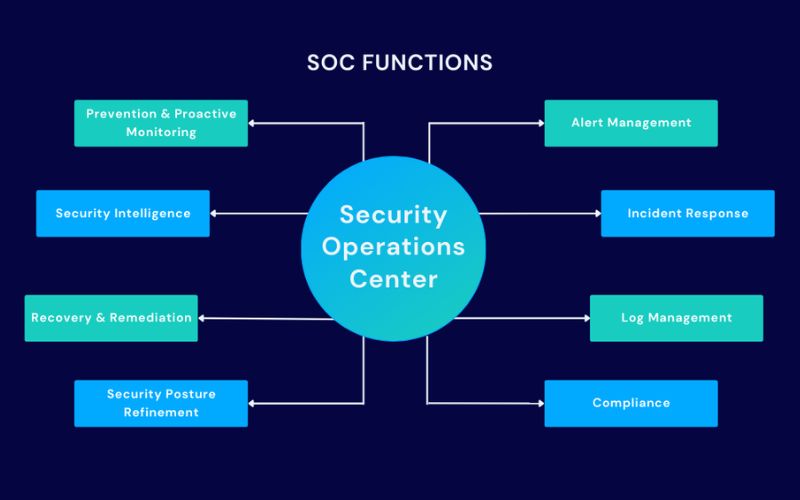
A security operations center may help mitigate the effects of a data breach, but its financial benefits extend well beyond that. Here are eight SOC advantages to think about.
1. Continuous protection
Security operations centers are open 24 hours a day, seven days a week. This continuous monitoring is crucial for spotting the earliest signals of unusual behavior. Attacks do not occur exclusively from 9 a.m. to 5 p.m., Monday through Friday. SOC team members, whether in-house, contracted, or virtual, continuously watch for possible vulnerabilities in order to detect attacks at all hours.
2. Quick and effective response
Because SOC team members continually watch for threats, the time passed between when the breach happened and the mean time to discovery is reduced. If unusual activity is identified, SOC analysts examine and confirm that the incident is truly an attack before attempting to control it. The SOC team then initiates an incident response to assess the severity of the threats, eliminate them, and mitigate any negative consequences.
3. Decreased costs of breaches and operations
By reducing the length of time a cyber attacker spends in an enterprise’s network, the SOC team may decrease the impact of a breach and, as a result, the possible expenses associated with the breach, such as data loss, litigation, or corporate reputation harm. The longer an attacker remains in a system, the greater the potential damage to the firm.
Furthermore, SOC teams work hard to minimize downtime and business interruption during an attack in order to avoid monetary losses.
A centralized SOC team can reduce Capex and Opex in terms of operations. focusing on a streamlined team of security professionals also prevents numerous organizations or departments from duplicating efforts by focusing on the same cybersecurity problems.
The SOC itself can be a cost-cutting measure. Outsourcing security duties to managed security service providers, cloud service providers, or virtual SOCs can obviate the requirement for a dedicated SOC facility and people.
4. Threat prevention
SOCs are used for more than simply event detection. SOC teams’ analysis and threat-hunting aid in the prevention of assaults in the first place. SOCs give organizations more visibility and control over security systems, allowing them to stay ahead of prospective attackers and concerns.
5. Security expertise
A SOC manager, incident responder, and security analyst(s), as well as additional specialized professions such as security engineers, threat hunters, forensic investigators, and compliance auditors, are common in a security operations center. Each of these professionals has a varied set of talents that, when paired with those of other SOC personnel, aid in the detection, remediation, analysis, and learning from threats.
Members of the team are also well-versed in tried-and-true threat detection and prevention technologies like SIEM, behavioral threat analytics, AI and machine learning, and cloud access security brokers, as well as the most sophisticated threat detection methodologies.
6. Communication and collaboration
A SOC team is skilled in communication and cooperation, not only within the team but also throughout the enterprise. SOC team members educate employees, third-party contractors, clients, and more about potential threats through security awareness training programs. Members of the security operations center also share security insights with C-level executives and management, business leaders, and department heads to assist company leaders in calculating potential risks and determining whether the risks should be accepted or a new policy or control should be implemented to mitigate them.
7. Compliance
Key SOC monitoring skills are critical to organizational compliance, particularly in the aftermath of rules requiring specific security monitoring activities and methods, such as GDPR and CCPA.
8. Improved business reputation
Having a SOC shows workers, clients, consumers, and third-party stakeholders that the organization is serious about data security and privacy. This makes it easier for the company, its workers, and its customers to share data. And the more a corporation takes data security and privacy seriously, the more trust it will acquire from its constituents. A well-managed SOC’s better corporate reputation may result in more referrals from existing and future clients.
Security Operations Center Job Roles

Of course, the SOC is completed by a number of particular jobs. Although precise job duties and titles vary in each company, the following are some of the job titles that are commonly seen in a SOC:
- Junior security analyst: This individual is in charge of frequently monitoring the security tools and apps that have been implemented and then offering valuable interpretations and context based on those reports. Intrusion detection system (IDS) apps, security information, and event monitoring (SIEM) applications, and cybersecurity threat feed applications are examples of these kinds of apps. This job title is sometimes known as an operator or SOC operator.
- Senior security analyst: This individual performs many of the same duties as a junior-level analyst but focuses on more difficult and urgent topics. A senior security analyst is frequently in charge of directing incident response actions. In fact, a senior security analyst is frequently referred to as an incident response manager.
- Threat hunter: This individual possesses a rare blend of security analytics and penetration testing abilities. A threat hunter can also collaborate with both technical and non-technical personnel to assist an organization to predict assaults.
- Cyber Threat Intelligence (CTI) manager: Many for-profit and non-profit organizations produce valuable threat intelligence feeds. A CTI manager may be assigned to gather, filter through, and evaluate these feeds for the organization.
- Manager: This individual is in charge of managing each team member as well as the technology that each team member employs.
How To Build And Maintain A SOC?
A SOC team’s members do not all have decades of security experience. Indeed, some SOC team members have only a few years of IT expertise. Others, though, have more.
A SOC team member’s fundamental attribute is simply a significant depth and breadth of expertise in all areas of IT, as stated in the table below. CompTIA certificates address the abilities required to work in a SOC, as listed below. A CompTIA certification demonstrates to companies that you have the expertise they require in their security operations center.
| Activity | Description | CompTIA Certification |
|---|---|---|
| Endpoint analysis | The ability to understand how a network host is supposed to behave and how it can be manipulated | CompTIA A+ |
| Network and cloud resource evaluation | Experience with how protocols can be misused | CompTIA Network+ CompTIA Cloud+ CompTIA Linux+ CompTIA Server+ |
| Vulnerability recognition and attack recognition | Practical, hands-on experience with exactly what an attack looks like | CompTIA Security+ |
| Analysis of Tactics, Techniques, and Procedures (TTPS) and Indicators of Compromise (IoC) | Ability to identify specific hacker activities | CompTIA Security+ CompTIA CySA+ CompTIA PenTest+ |
| Following each step of the hacker lifecycle | Detailed ability to trace how a hacker pivots while making an attack; requires knowledge of various models, including the Lockheed-Martin Cybersecurity Kill Chain, the MITRE ATT&CK model, and the diamond model | CompTIA Security+ CompTIA PenTest+ |
It’s important to note that entry-level SOC analysts may not require advanced certifications like CompTIA Cybersecurity Analyst (CySA+), CompTIA PenTest+, or CompTIA Advanced Security Practitioner (CASP+). But the table above should give you an idea
How To Choose The Right SOC Model?

It may be simplest for organizations to begin with a fully outsourced SOC. Starting a SOC presents several deployment, training, and operational problems. Attempting to establish an internal SOC from the ground up (or combining existing SOCs through a merger or purchase) without assistance may result in a lesser value proposition than planned.
The most important concerns for firms that currently have an internal SOC and are debating whether to entirely outsource or go with a hybrid model are the amount of autonomy necessary (more autonomy favors a hybrid model) and cost. (lower cost favors a fully outsourced model).
Consider the following while creating a completely insourced SOC:
- Budget overruns of about 30% are to be expected.
- Allow for additional time than was initially allocated before the SOC is completely operational.
Using an outsourced or hybrid SOC, in which the outsourced provider implements and maintains the SIEM, reduces time and cost overruns. This works if the fees are agreed upon in advance and the outsourced supplier has expertise with SIEM implementations, which allows it to avoid frequent mistakes.
FAQs

Who Benefits from Security Operations Center as a Service Most?
Only the larger firms that face frequent cyberattacks hire a specialized SOC. However, the related expenses will almost certainly force conventional, organization-exclusive teams to adopt a hybrid approach, even if the majority of operations stay in-house.
What are the 3 components of a security center?
The CIA triad is a three-part information security concept that includes confidentiality, integrity, and availability. Each component reflects a key information security goal.
What is the difference between SIEM and SOC?
The primary distinction between a SIEM and a SOC is that a SIEM gathers and correlates data from several sources, whereas a SOC collects data from multiple sources and forwards it to a SIEM.
What are the top 3 SOC?
You may read the finest SOC as a Service Solutions user reviews to help you pick which solution has the finest features for you and your company.
- Arctic Wolf AWN CyberSOC is ranked first.
- Alert Logic is number two.
- Netsurion Managed Threat Protection is ranked third.
How many levels of SOC are there?
Three distinct kinds
The AICPA distinguishes three types of SOC reports. Understanding the distinctions between SOC 1 vs SOC 2 vs SOC 3 is critical when determining which sort of compliance is required for your company.
Final Words
In conclusion, a Security Operations Center (SOC) is an essential component of an organization’s cybersecurity strategy. Its role in monitoring, detecting, and responding to security incidents cannot be overstated. By establishing a SOC, organizations can proactively identify and mitigate potential security risks, thereby safeguarding their critical assets.
In this guide, we have covered the fundamentals of a SOC, including its functions, processes, and benefits. We hope that this has provided you with a better understanding of “What is a Security Operations Center?“ and why it is crucial to modern-day businesses.
Remember, cybersecurity threats are becoming increasingly sophisticated and frequent. As such, it is imperative that organizations take proactive measures to protect themselves. By establishing a Security Operations Center, businesses can stay ahead of potential threats and ensure the continued integrity, confidentiality, and availability of their information assets.
[Sassy_Social_Share]


