If you’re capturing packets and analyzing network traffic, you’re probably using Wireshark. But what is the use of Wireshark? How does Wireshark troubleshoot network difficulties? And who might gain the most from it? In this article, IT Exams will discover all of those pieces of information to help you gain a better understanding of Wireshark!
What Is Wireshark?

Wireshark is a network protocol analyzer or an application that captures packets from a network connection, such as the one connecting your computer to your home office or the internet. A packet is a distinct unit of data in a standard Ethernet network. Wireshark is the world’s most popular packet sniffer.
Wireshark has various applications, including debugging network performance concerns. Wireshark is frequently used by cybersecurity experts to trace connections, analyze the contents of suspicious network transactions, and spot surges of network traffic. It’s an important aspect of any IT professional’s toolset – and preferably, the IT expert knows how to utilize it
How Does Wireshark Work?
Wireshark is a packet analyzer and sniffer. It records network traffic from ethernet, Bluetooth, wireless (IEEE.802.11), token ring, and frame relay connections, among others, and stores it for further study.
Wireshark allows you to filter the log before or during capture to narrow down and zero in on what you’re searching for in the network trace. For example, you may configure a filter to only display TCP traffic between two IP addresses, or you can configure it to only show packets transmitted from one device. Wireshark’s filters are one of the key reasons it has become the industry standard for packet analysis.
What Is The Use Of Wireshark?
Wireshark is sometimes compared to a flashlight – a useful tool that allows you to see what you’re doing more clearly and is very necessary if you’re going to be working on a car at night or exploring a wild region. With one, you can spot risks and highlight items you would have missed otherwise.
Administrators primarily use Wireshark to troubleshoot network performance issues. If you observe a spike in latency, lost packets, retransmission difficulties, or a malicious threat on your network, you may use Wireshark to investigate.
You’ll be able to investigate issues as they arise with Wireshark’s analysis to determine what’s causing them. Of course, Wireshark facilitates this by converting the traffic it records into a comprehensible format, as people have difficulty understanding binary. With this information, you can examine your traffic in more depth, analyzing the type of traffic as well as its frequency, quantity, and latency.
If you observe a spike in latency, lost packets, retransmission difficulties, or a malicious threat on your network, you may use Wireshark to investigate.
When it comes to who utilizes Wireshark, you might be surprised at how widely it is used in many digital fields. Businesses, institutions, technologically adept individuals, and even the government use
When it comes to who utilizes Wireshark, you might be surprised at how widely it is used in many digital fields. The tool is used by businesses, schools, tech-savvy individuals, and even the government. Part of Wireshark’s allure stems from the fact that it’s a terrific method to learn more about how network traffic works in the first place, as well as how to troubleshoot issues that arise.
To use Wireshark efficiently, you must first understand the fundamentals of networking. Knowledge of routing and port forwarding, as well as the three-way TCP handshake, the TCP/IP stack, and a range of protocols such as TCP, UDP, DHCP, and ICMP, would be excellent.
When Should Wireshark Be Used?
Wireshark is a secure network troubleshooting tool used by government organizations, educational institutions, enterprises, small businesses, and NGOs alike. Wireshark may also be used as a learning tool.
Those new to information security may use Wireshark to learn about network traffic analysis, how communication works when certain protocols are used, and where things go wrong when problems arise.
Wireshark may be used to understand how communication occurs over a network and to determine what went wrong when a communication problem emerges.
Wireshark is useful:
- Network administrators tackle network issues.
- Security engineers investigate security concerns within a network.
- Applications are tested by QA engineers.
- Protocol implementations are tested by developers.
- Users of the network learn about a certain protocol.
When Should Wireshark Not Be Used?
Wireshark, obviously, cannot do everything.
First and foremost, it cannot assist a user who is unfamiliar with network protocols. No instrument, no matter how wonderful, can completely replace knowledge. In other words, in order to use Wireshark effectively, you must first understand how a network works. That means you’ll need to know about things like the three-way TCP handshake and other protocols including TCP, UDP, DHCP, and ICMP.
Second, Wireshark cannot normally capture communication from all of the other systems on the network. Wireshark (or any other standard packet-capturing program) can only sniff communications between your local computer and the remote machine it is communicating with on current networks that utilize switches.
Third, while Wireshark may display faulty packets and use color coding, it lacks genuine alarms; it is not an intrusion detection system. (IDS).
Fourth, Wireshark cannot assist with the decryption of encrypted communications.
Finally, it is relatively simple to spoof IPv4 packets. Wireshark cannot tell you if an IP address found in a recorded packet is valid or not. This necessitates a little more know-how on the side of an IT professional, as well as extra software.
How To Use Wireshark
Wireshark is available for free download at www.wireshark.org. It’s also available for free as an open-source program licensed under the GNU General Public License version 2.
How to Install Wireshark on Windows
If you use the Windows operating system, download the version that corresponds to your version. If you’re using Windows 10, for example, you’d download the 64-bit Windows installer and run the installation procedure. Administrator privileges are required for installation.
Wireshark for Mac
Wireshark is available as a Homebrew install on the Mac.
To install Homebrew, type the following command into your Terminal prompt:
/usr/bin/ruby -e “$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)”
Once you’ve installed the Homebrew system, you’ll be able to access a variety of open-source projects for your Mac. Run the following command from the Terminal to install Wireshark:
Install Wireshark using brew
Wireshark and any dependencies required for proper operation will be downloaded and installed by Homebrew.
How to Install Wireshark on Linux
If you have a Linux machine, you would install Wireshark in the following order (note that you would require root permissions):
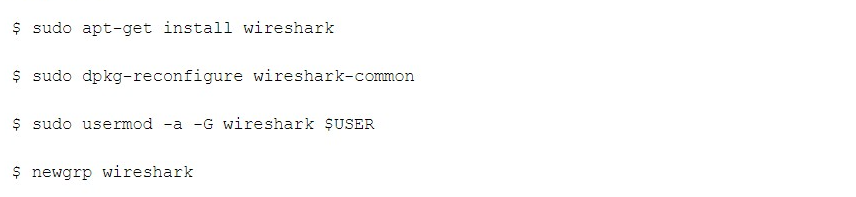
Once you have completed the above steps, you then log out and log back in, and then start Wireshark:

Color Coding In Wireshark
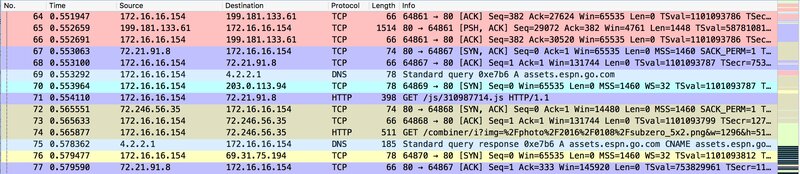
Now that you have some packets, you must decipher what they mean. Wireshark uses common-sense color coding to assist you in identifying packet kinds. The table below describes the default colors assigned to the most common packet types.
| Colors in Wireshark | Packet Types |
|---|---|
| Black | Packets with errors |
| Light blue | UDP |
| Light purple | TCP |
| Dark yellow | Routing |
| Light yellow | Windows-specific traffic, including Server Message Blocks (SMB) and NetBIOS |
| Light green | HTTP traffic |
| Dark gray | TCP SYN, FIN, and ACK traffic |
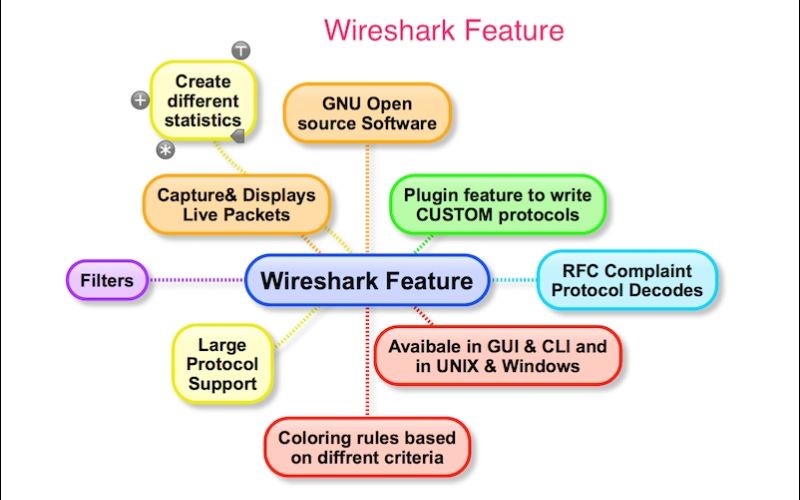
What Are Some Features Of Wireshark?
The following are some of the numerous functionalities offered by Wireshark.
- Deep examination of hundreds of procedures, with more being added on a regular basis
- Offline analysis and live capture
- Typical three-pane packet browser
- Multi-platform: Runs on Windows, Linux, OS X, FreeBSD, NetBSD, and a variety of other operating systems.
- Captured network data may be viewed using a GUI or the TTY mode. The TShark utility
- The industry’s most powerful display filters
- Comprehensive VoIP analysis
- Many distinct capture file types may be read and written: tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, NetScreen snoop, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar
- Surveyor, Tek EtherPeek/TokenPeek/AiroPeek, to name a few.
- Gzip-compressed capture files can be decompressed on the fly.
- Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and more protocols may be read in real-time. (depending on your platform)
- Many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2, provide decryption capabilities.
- For rapid, straightforward analysis, coloring rules can be applied to the packet list.
The output can be saved as XML, PostScript®, CSV, or plain text.
Data Packets On Wireshark
Capturing data packets on Wireshark
When you launch Wireshark, you’ll get a list of all the network connections you can monitor. You may also use the capture filter field to collect only the network traffic you wish to view.
Using shift+left-click, you may pick one or more network interfaces. After selecting the network interface, you can begin the capture in one of three methods.
Click the “Start capturing packets” button on the toolbar.
Select Capture -> Start from the menu.
You might also use the keyboard shortcut Control+E.
Wireshark will display the captured packets in real time during the capture.
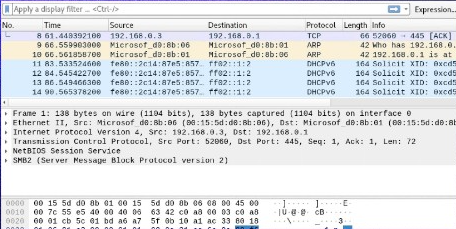
Once you’ve captured all of the required packets, use the same buttons or menu choices to end the capture that you used to start it.
Stopping Wireshark’s packet capture before analyzing is best practice.
Analyzing data packets on Wireshark
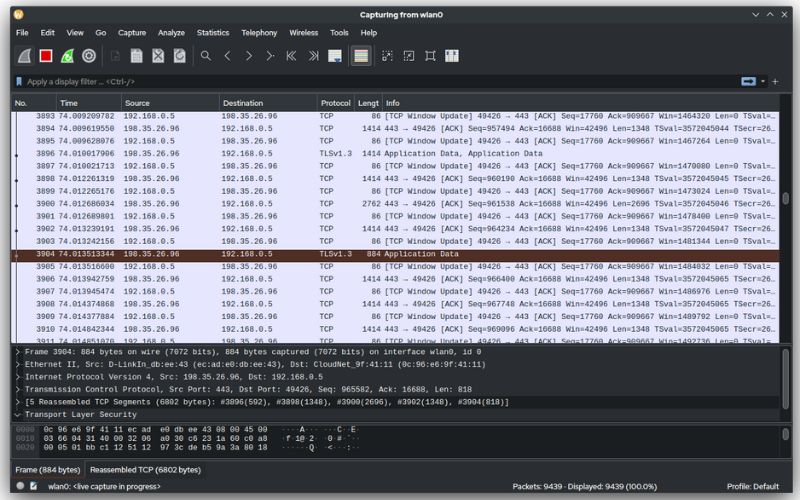
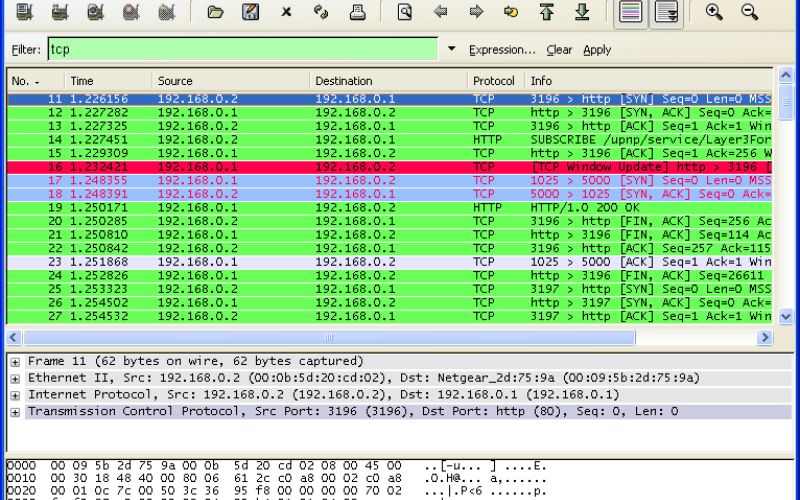
Wireshark displays three panels for examining packet data. The top pane, the Packet List, displays a list of all the packets in the capture. When you click on a packet, the other two windows shift to display the packet’s information. You may also determine whether the packet is part of a discussion. Here are the specifics for each column in the top pane:
- No. : This is the packet capture’s numerical order. It is part of a dialogue, as shown by the bracket.
- Time: This column indicates how long this particular packet was collected after you started the capture. To display a different choice, adjust this value in the Settings menu.
- Source: The source address is the system address that transmitted the packet.
- Destination: This is the address of the packet’s destination.
- Protocol: This is the packet’s protocol. TCP, DNS, DHCPv6, and ARP are a few examples.
- Length: This column displays the packet’s length in bytes.
- Info: This column displays additional information about the packet’s contents, which varies based on the kind of packet.
The center pane, Packet Details, displays as much legible information about the packet as feasible, depending on the packet type. You may build filters based on the selected text in this field by right-clicking.
The Packet Bytes window at the bottom displays the packet in hexadecimal format.
When viewing a packet that is part of a discussion, right-click the packet and select Follow to see only the packets in that conversation.
Wireshark Filters
The capture filters and display filters are two of Wireshark’s strongest features. Filters enable you to see the capture in the manner required to troubleshoot the difficulties at hand. Here are a few filters to get you started.
Wireshark capture filters
Capture filters limit the captured packets based on the filter used. Wireshark will not store packets that do not match the filter. Capture filters include the following:
- host IP address: This filter restricts traffic to and from the IP address.
- net 192.168.0.0/24: This filter collects all network traffic.
- dst host IP-address: Capture packets transmitted to the given host.
- port 53: Only capture traffic on port 53.
- port not 53 and not arp: Except for DNS and ARP traffic, capture all traffic.
Wireshark display filters
During analysis, Wireshark display filters modify the perspective of the capture. After you’ve paused the packet capture, utilize display filters to limit down the packets in the Packet List to help you solve the problem.
The following is one of the most helpful display filters:
ip.src==IP-address and ip.dst==IP-address
This filter displays packets sent from one machine to another (ip.src). (ip.dst). You can also use ip.addr to view packets sent and received by that IP address. Other filters are:
tcp.port eq 25: This filter will display all traffic on port 25, which is typically used for SMTP communication.
icmp: This filter will display just ICMP traffic in the capture, which is most likely pings.
ip.addr != IP_address: This filter displays all traffic except that too and from the specified machine.
Analysts may also create filters to identify specific assaults, such as this one for detecting the Sasser worm:
ls_ads.opnum==0x09
Additional Wireshark Features
Aside from capture and filtering, Wireshark has various more functions that might help you out.
Wireshark colorization options
Wireshark may be configured to color your packets in the Packet List based on the display filter, allowing you to accentuate the packets you wish to highlight.
Wireshark promiscuous mode
Wireshark may be configured to color your packets in the Packet List based on the display filter, allowing you to emphasize specific packets. Here are a few examples.
Wireshark command line
If you use a system without a graphical user interface, Wireshark has a command line interface (CLI). (GUI). The ideal practice would be to capture and store a log using the CLI so that you may evaluate it with the GUI.
Wireshark commands
- wireshark : run Wireshark in GUI mode
- wireshark –h : show the possible command line parameters for Wireshark
- wireshark –a duration:300 –i eth1 –w wireshark. : Once every five minutes, collect traffic on the ethernet port. -a indicates that the capture should be stopped automatically, and -i specifies the interface to capture.
Additional Wireshark Resources And Tutorials
There are several tutorials and videos available that demonstrate how to utilize Wireshark for certain applications. You should start your search on the main Wireshark website and work your way down. There is also official documentation and a Wiki on that site.
Wireshark is a fantastic network sniffer and analysis tool, but it’s best utilized when you know exactly what you’re searching for. Because there is too much noise on the network, you won’t be able to use Wireshark to uncover a new problem. Varonis with Edge will assist you in making sense of the overall issue and pointing you to a threat to examine; you will then use Wireshark to delve further to comprehend the threat contained within the packet.
When Varonis security researchers identified the Norman crypto miner, they received alerts from many devices indicating unusual network and file activity. During the crypto miner examination, Varonis researchers utilized Wireshark to monitor network activity for some of the problematic computers. The research team discovered that a new crypto miner known as Norman was actively talking with command and control (C&C) servers via DuckDNS using Wireshark. With Wireshark, the Varonis team was able to view all of the IP addresses of the attackers’ C&C servers, allowing the firm to cut contact and therefore end the attack.
FAQs
Who created Wireshark?
Mr. Gerald Combs did.
Gerald Combs needed a tool to hunt down network problems and wanted to learn more about networking in late 1997, so he began building Ethereal (the original name of the Wireshark project) to solve both concerns.
Can Wireshark capture passwords?
Many individuals are curious whether Wireshark can collect passwords. The answer is unequivocal yes! Wireshark can capture any sort of data flowing via a network, including usernames, email addresses, personal information, images, videos, and anything else.
Why do hackers use Wireshark?
Footprinting and reconnaissance: Before launching an active assault, hackers use Wireshark to collect unencrypted data in order to learn as much as possible about the target.
What are the four main uses of Wireshark?
Wireshark is an open-source packet analyzer that is free to use. It is used for network troubleshooting, analysis, the creation of software and communications protocols, and teaching.
How do I monitor my network with Wireshark?
Steps:
- Install Wireshark.
- Launch your web browser.
- Clear the cache in your browser.
- Launch Wireshark.
- Select “Capture > Interfaces”…
- You’ll want to record all traffic that passes through your ethernet driver.
- Go to the URL from which you intended to capture traffic.
Final Words
In conclusion, Wireshark is an essential tool for network troubleshooting, protocol analysis, and security testing. By capturing and analyzing network traffic, it allows users to gain a better understanding of how their network operates, identify and diagnose issues, and detect potential security threats.
Whether you are a network administrator, a security analyst, or a developer, knowing what is the use of Wireshark and how to use it effectively can significantly improve your ability to troubleshoot, optimize, and secure your network. With its rich feature set, intuitive user interface, and extensive documentation, Wireshark is the go-to tool for network analysis and monitoring.
So, whether you’re looking to diagnose network issues, debug protocols, or analyze traffic patterns, Wireshark is an indispensable tool that every network professional should have in their toolkit. With its powerful capabilities and user-friendly interface, it provides a comprehensive solution for capturing, analyzing, and interpreting network traffic, making it an invaluable resource for anyone involved in network administration or security. With this guide on “What Is The Use Of Wireshark?“, we hope you find helpful information for yourself. Goof luck!
[Sassy_Social_Share]


